To be able to create accounts quickly, Flexopus can be integrated into already existing environments.
Topics
- Federated authentication
- What are the advantages of SCIM?
- Integration with Azure Active Directory
- Other
Federated authentication
You can integrate with Microsoft Azure Active Directory (Azure AD) via federated authentication or using SCIM (System for Cross-domain Identity Management), allowing users to log in to Flexopus using their existing Azure AD credentials.
Flexopus can be linked to an instance of Microsoft Azure Active Directory (Azure AD) via federated authentication. This is a process whereby the username and password of an account from a first directory system are provided in such a way that the same username and password can also be used in other systems.
What are the advantages of SCIM?
With the SCIM interface, you can better automate user administration between your iDP (Identity Provider) and us as SP (Service Provider). The following advantages result from this:
- Synchronise and deploy user groups
You can manage user groups externally in your iDP. Through SCIM, external groups including members can be sent to Flexopus. These groups are created in Flexopus as "read-only" groups and can only be managed externally by your iDP. The groups can then be used normally for the administration of the workstations. All changes in these groups are sent to Flexopus within 40 minutes. - Synchronise and provide user profiles
User profiles and the changed and associated attributes (name, job title, department, etc.) can be synchronised automatically. Every change in your iDP is usually sent to Flexopus within 40 minutes, so user profiles can be kept constantly up-to-date. In contrast to SAML2, the data exchange runs during the session time and not only during the login attempt. - User profiles before the first login
By combining the two benefits, you can basically create a group in your iDP. You can assign group to Flexopus. Through this assignment, the members of the group can also be sent to Flexopus before the first login.
Example: The newly hired employees can be sent to Flexopus before the first working day, so that the responsible colleagues can possibly manage local user groups in Flexopus. - Automatically archive and delete user profiles
The provided user profiles including group assignments can also be automatically deactivated / archived. Should a staff member lose access to the application. The iDP reports through SCIM to Flexopus that the employee no longer has access to the application. This can happen for several reasons: Employee was dismissed or the IT Administrator has intentionally or unintentionally revoked the authorisation. Thus, the employee is archived in Flexopus. With an additional data protection setting, the archived users can then be automatically deleted from Flexopus after X days.
BEST PRACTICE, for user groups
The fact that you can synchronise user groups through SCIM does not mean that you have to map all user groups in the iDP. We recommend a healthy use of user groups. As a rule, our customers configure the groups as follows:
Example Company A:
Only one group is created by SCIM: Flexopus All User. The employees are collected in this group and made available to Flexopus. Facility management takes care of the rest of the group management locally in the Flexopus dashboard. Typically, this solution is chosen when IT reacts "too slowly" and facility management wants "more flexibility".
Example Company B:
Meaningful groups that might also be relevant for other applications company-wide are maintained in the iDP. Example: Larger departments with at least 25 users, subsidiaries and/or business units. These groups are provided automatically and maintained by IT. The other user groups, which only make sense in the facility management context, are created and maintained locally in Flexopus. Example: Workgroup Department A Cluser 2.
Integration with Azure AD
1. Create a SCIM token in the Flexopus Single Sign On Settings and copy it.
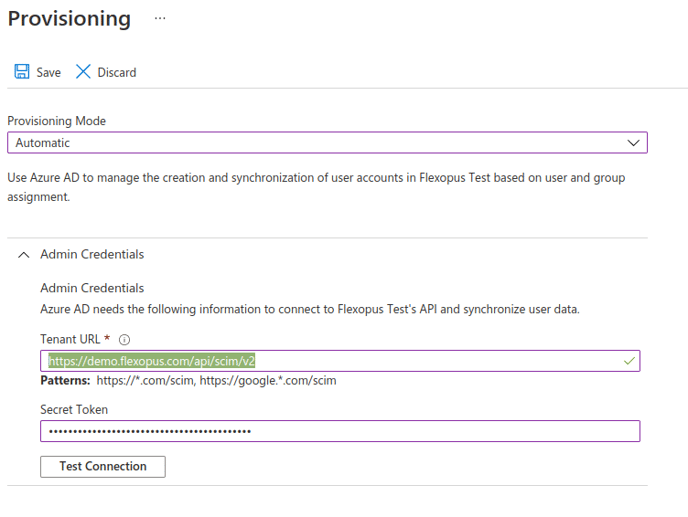
2. On the Provisioning tab in the configuration of your enterprise application in Azure, select Get started.
3. Configure your deployment details.
- Set the Provisioning Mode to Automatic
- Set the Tenant URL to https://{your-flexopus-domain}/api/scim/v2
- Paste the previously copied Secret Token
4. Set up the attribute mappings: Select provision Azure Active Directory Users
5. Configure the user assignments
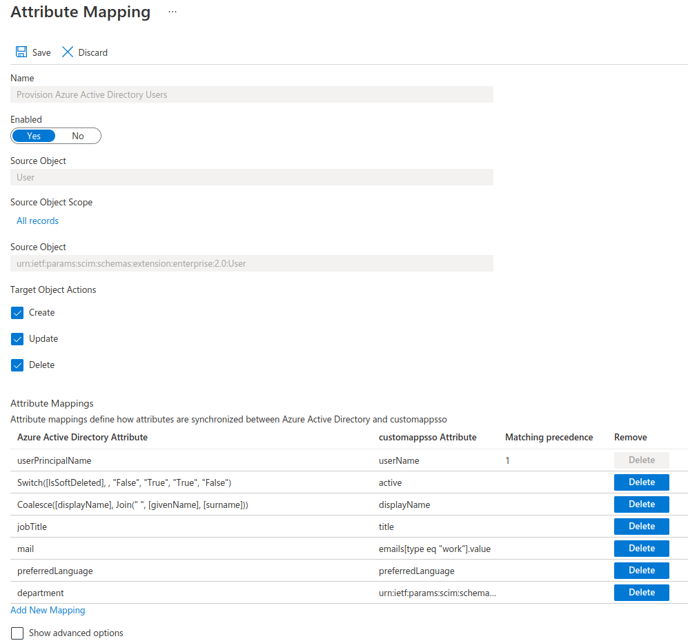
Remove all assignments except:
- userPrincipalName
- Switch([IsSoftDeleted], , "False", "True", "True", "False")
- displayName
- jobTitle
- preferredLanguage
- department
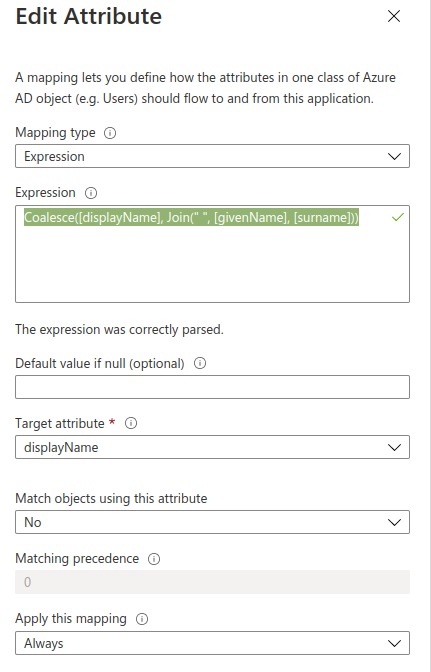
Update the assignment displayName
- Set the Mapping type to Expression
- Set the Expression to Coalesce([displayName], Join(" ", [givenName], [surname]))
The finished configuration should look like the following:
TIP: In principle, you can also use an attribute other than userName (upn). Depending on the user management, you can also use a field other than upn. It is important that the field always remains unique.
Suppose you use the externalId attribute instead of userPrincipalName. In this case, you can link the externalId as an Azure Active Directory attribute with the customappsso attribute field, i.e. simply replace the userPrincipalName with externalId.
With this setting, the SAML2 SSO installation must also be adjusted. User Attributes & Claims > change upn source attribute to user.externalId.
You can also use another field instead of externalId as upn. Only the example was carried out with the externalId.
6. Under Provisioning Azure Active Directory Users choose Source Object Scope > All records.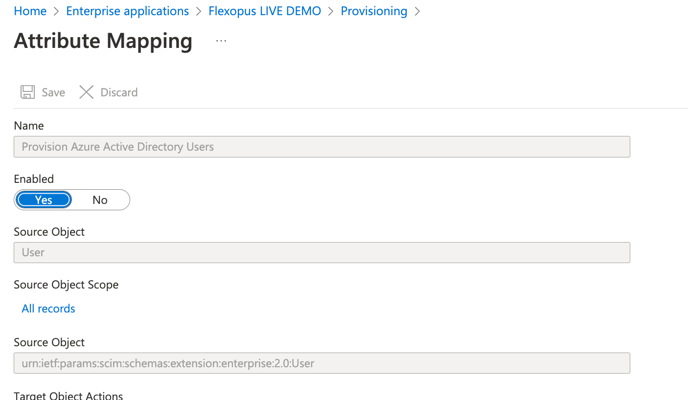
Only user profiles with existing email adresses are to be synchronised. Add Scoping Target Attribute: mail, Operator: IS NOT NULL. You have to save multiple times!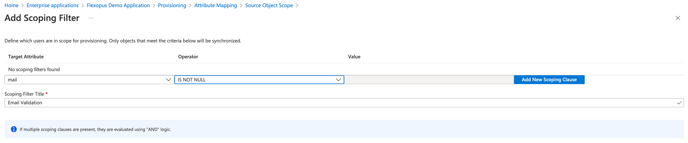
7. Turn on Provisioning by clicking on Start provisioning.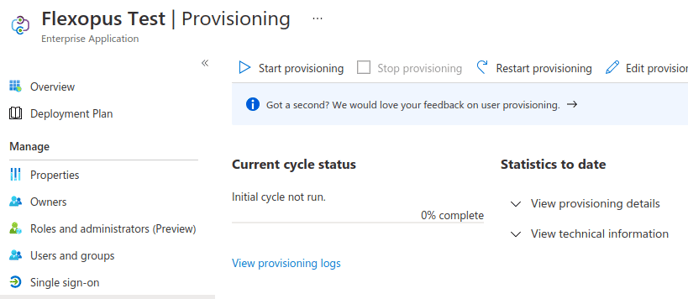
8. Finally, you need to link the user profiles and user groups (flat groups) to Flexopus so that user provisioning can start.
9. (optional) Click on Update credentials and enter our email address scim@flexopus.com. Please also activate "Send an email notification when a failure occurs" in the settings. This setting automatically informs us about possible synchronisation problems.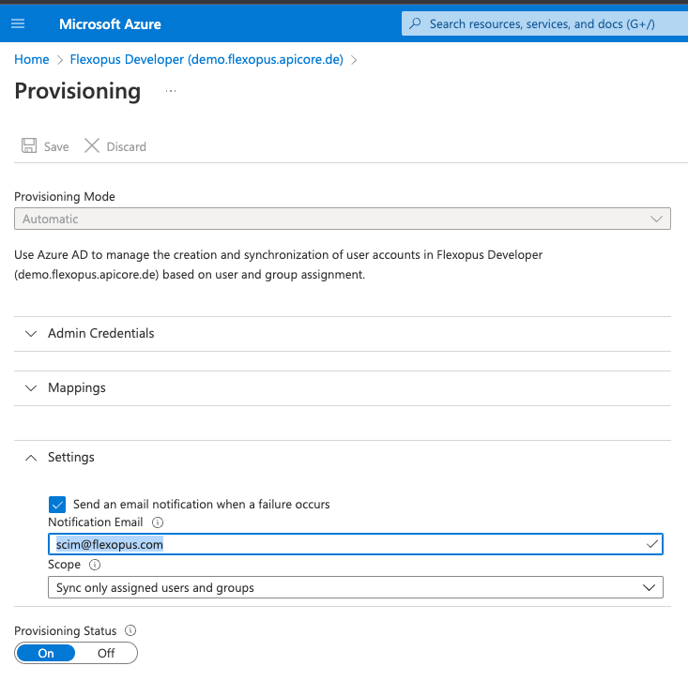
BEST PRACTICE, to synchronise all user profiles
Create a group or use an existing group to which the desired AD users are linked. Link the AD group to Flexopus.
The group and also the associated user profiles are created by SCIM in Flexopus before the first SAML2 login.
SCIM FIRST:
SCIM uses an own id to identify the users. The upn will be simple updated. no double entries will be created.
SAML FIRST
A - Logged in in the past
The user has a provider ID and the user will be found based on that.
B - Never logged in
The user has no provider ID yet, becacuse he never logged in with SAML2 before. The system tries to identify the user based on the upn, since the upn chnaged, the SAML2 will not ind him, BUT. As a last resort our system will try to identify the user based on the email address.
OAuth -> SAML2 change
Login type MS, Looking based on the provider id, login type = Microsoft and not OAuth then he tries to use upn, than email, than create new.
R0085