Update SAML2 Certificate
Overview
Using the SAML2 Singe Sign On integration, you can connect your Identity Provider with Flexopus (Service Provider) and ensure a smooth login experience for your users. The data is exchanged between the Flexopus and your Identity Provider securely. A certificate is shared with Flexopus to ensure this secure communication. The certificates have an expiration date, depending on your security settings, it can expire in 1 year, 3 years or in some cases in 5 years.
Your system administrator issues a new certificate after the old one is getting expired. The new certificate needs to be shared with Flexopus to ensure a seamless single sign in functionality.
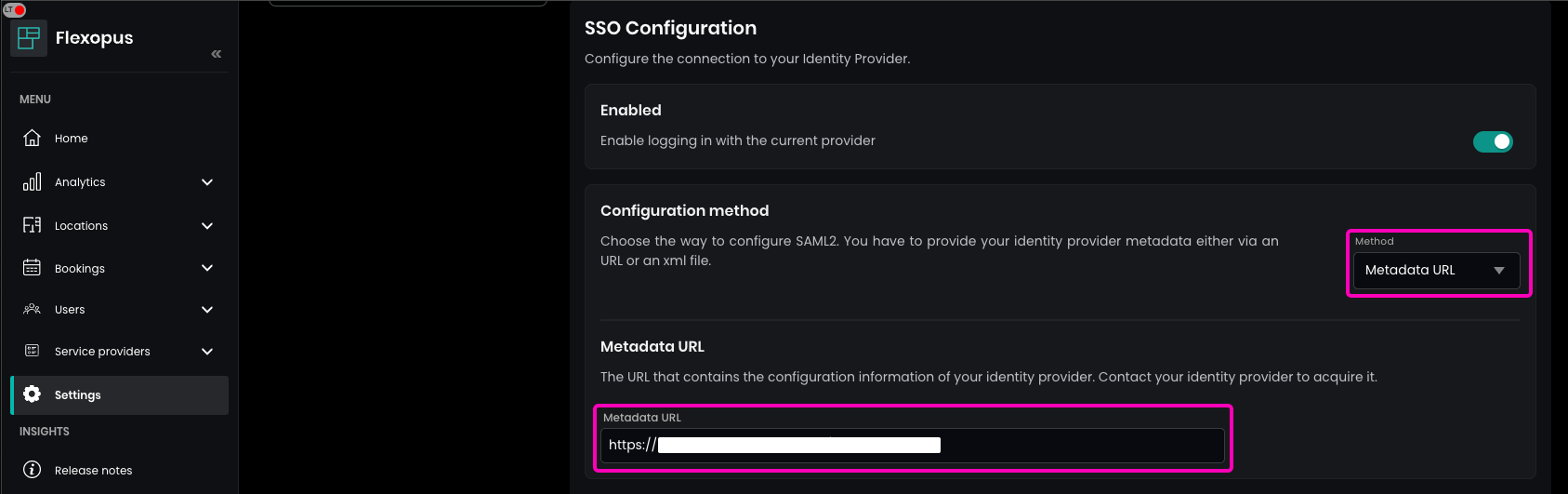
Flexopus offers two ways to configure the SAML2 SSO:
- Metadata URL
- Metadata file
SAVE.The metadata file includes the current certificate. Usually, it's the long texts between the X509Certificate elements:
<X509Certificate>XYZXYZ...</X509Certificate>
Metadata URL (recommended)
If you configured the metadata file with a URL, then the URL is basically pointing to the current metadata file. Flexopus is fetching the file once a day and caching it on the server. In case, the metadata file changed, Flexopus will fetch the data within 24 hours. In case you want to fetch the file faster, go to the SAML2 SSO configuration page in Flexopus, select the configuration and SAVE. Saving the configuration will trigger the fetching process and will update the certificate.
--
This configuration is used mostly by customers using Microsoft Azure Active Directory:
Metadata File
In some cases, the there is no metadata URL, due to a security configuration or due to a lack of functionality in your Identity Provider. In this case, the metadata is uploaded as a file into Flexopus. In this case, the current certificate is in the metadata file. If a new certificate is issued, Flexopus will know nothing about it, unless you upload the new metadata file with the new certificate into Flexopus.
--
This configuration is used mostly by customers using Microsoft AD FS or Google Workspace:
Recommendation
Generally, it's recommended to update certificates in an overlapping way. The old certificate should be still valid for a few days, weeks parallel to the new certificate. This way, the external systems such as Flexopus will be able to update the certificates in a reasonable time, and you are not breaking the integrations immediately. Due to our experience, not all Identity Providers are providing the functionality to have multiple valid certificates parallel. Try to overlap the certificates in case of an update, if technically possible.


