Ping Identity SAML2 + SCIM

Introduction
Connect Flexopus with Ping Identity via a SAML2 for Single Sign-On (SSO). With the integration, you can manage through your Ping Identity which users should have access to Flexopus and force them to use their Ping credentials for the login. Based on a SAML2 settings in Flexopus you can let the user profiles be created after the first successful SAML2 SSO login attempt to avoid a manual user creation process at Flexopus.
Ping Identity provides federated identity management and self-hosted identity access management (IAM) solutions to web identities and Single Sign-On solutions, being one of a number of organizations competing to provide standards to replace passwords for authenticating to web applications.
Setup Instruction Manual
Follow the step by step introduction manual to configure the integration. The manual also includes best practices and solutions for some commonly made errors during the configuration. Still, if you need help with the setup, feel free to reach out to our support team via support@flexopus.com.
STEP 1 - Create SAML2 app
Go to your Ping Identity admin console and navigate to the Connectors Tab
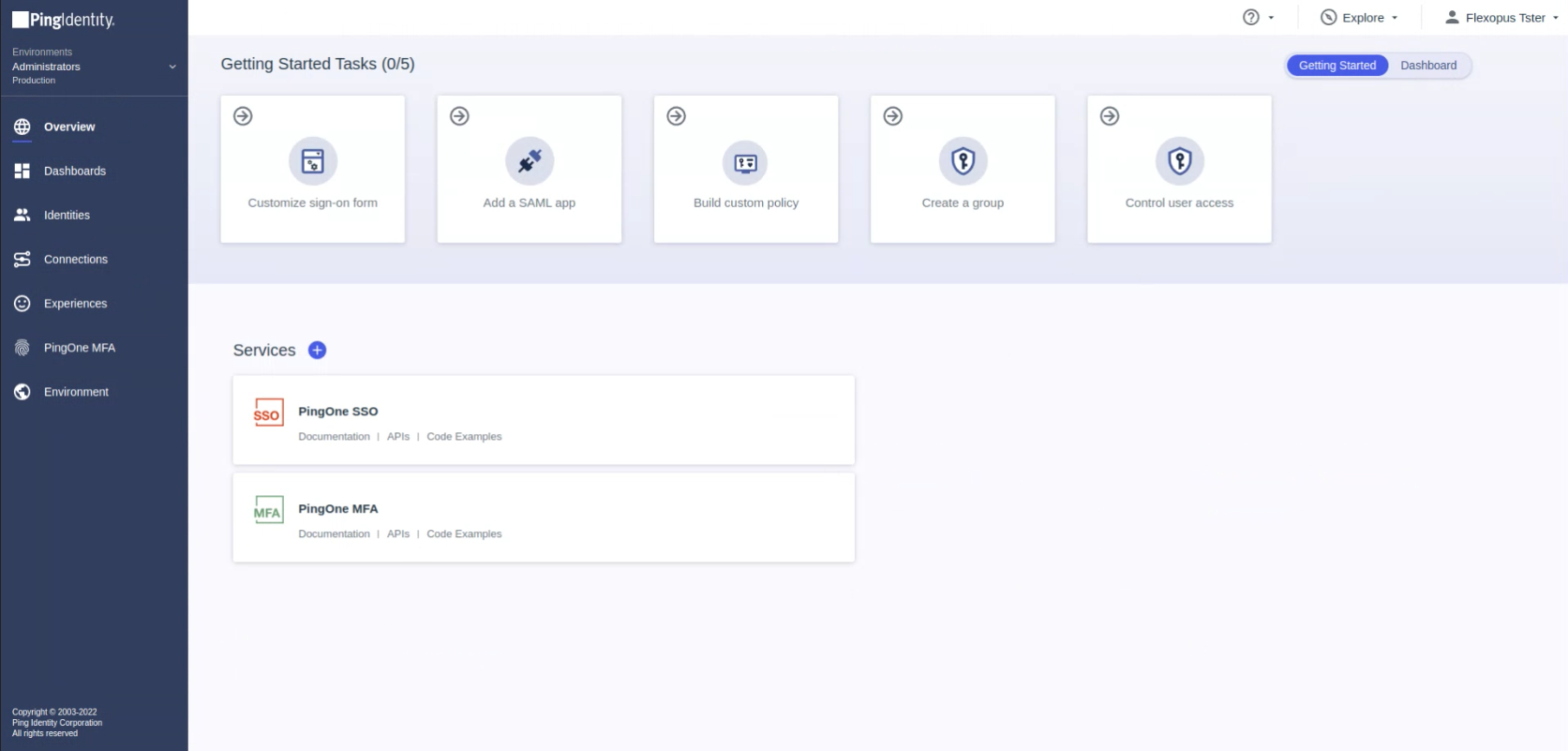
Select the Applications menu point and click on the add button in the top to create a new application.
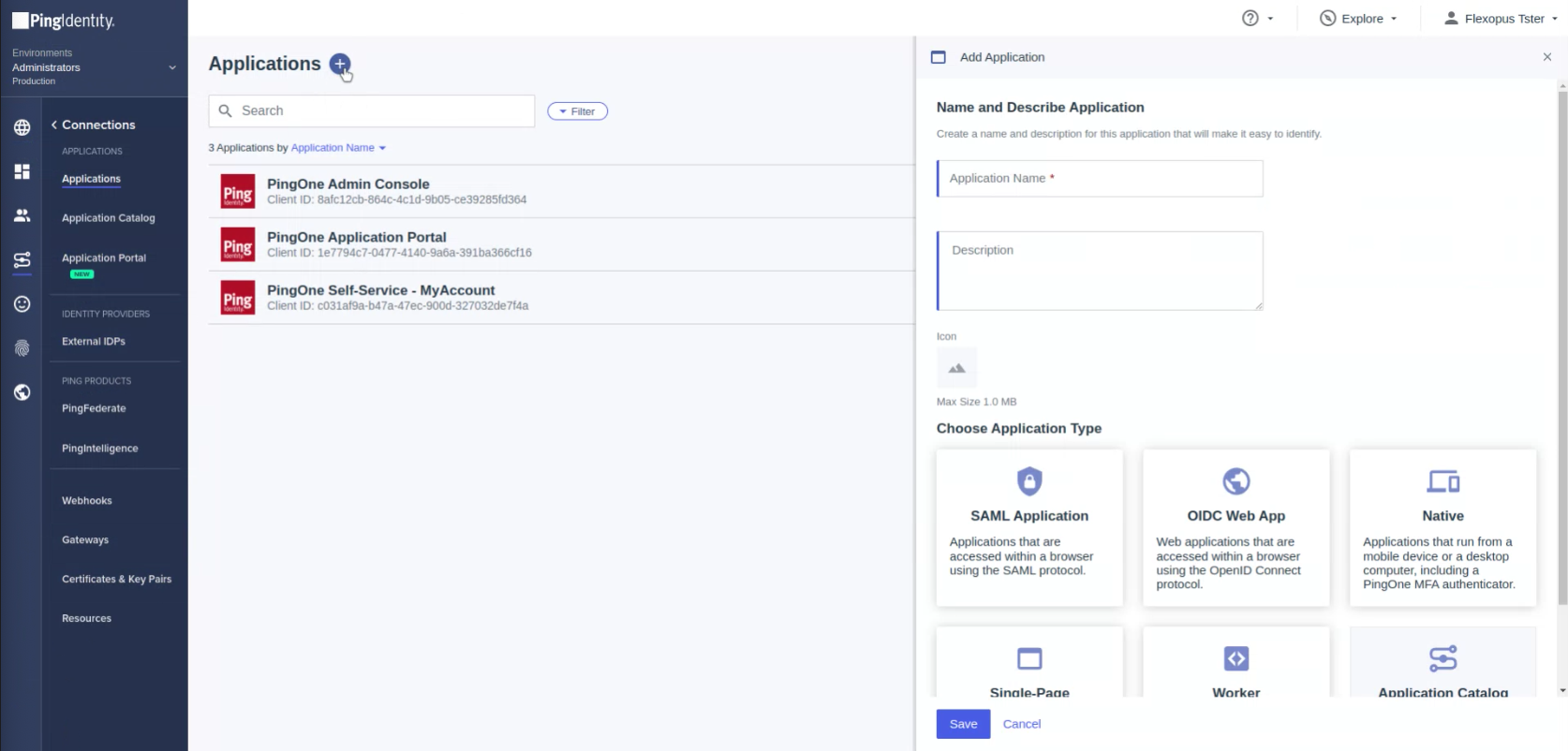
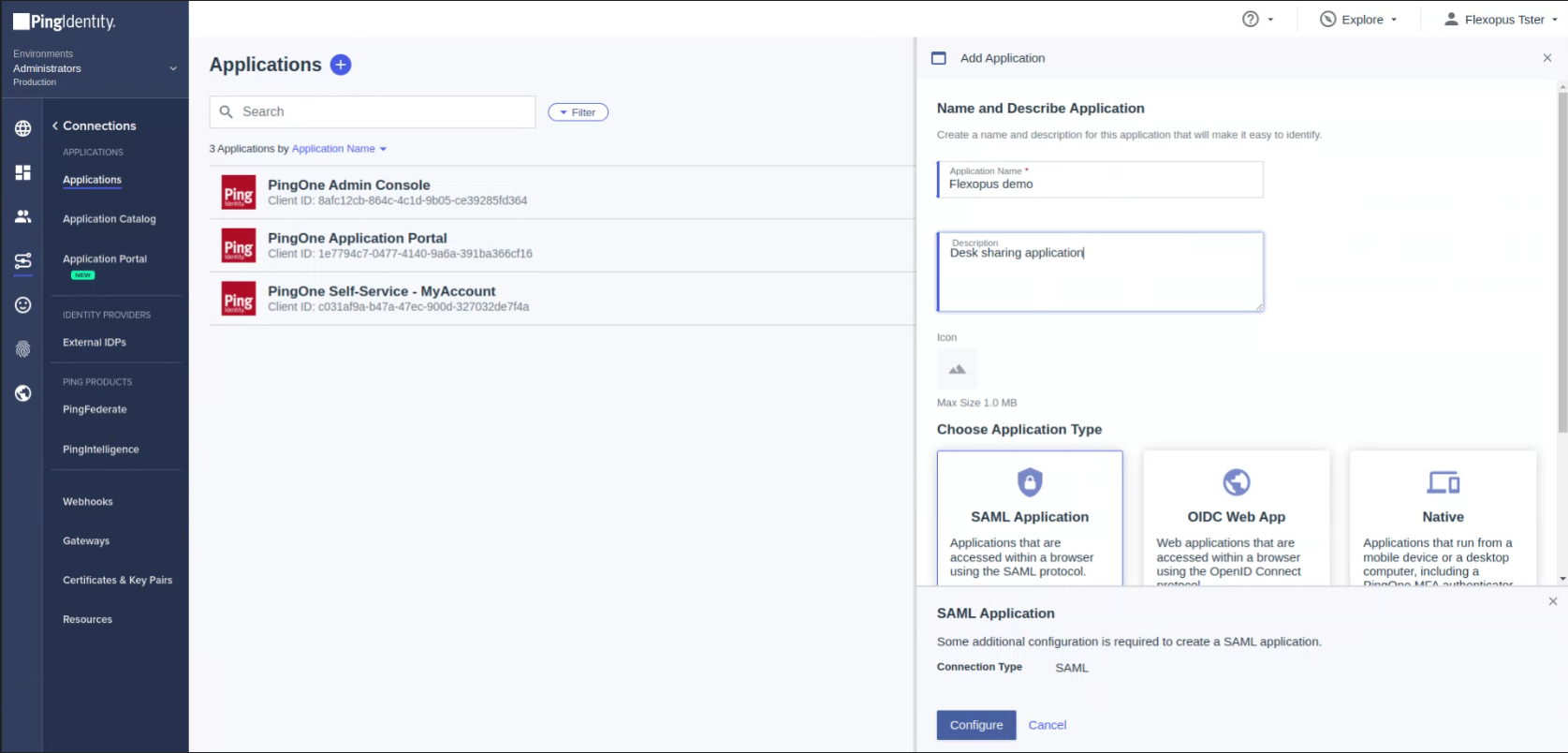
Enter the following parameters:
Name: Flexopus
Description: Desk Sharing Software
Select: SAML Application
On the SAML configuration page, enter the metadata URL of Flexopus. You can find this URL by navigating to Dashboard > Settings > Authentication in Flexopus as an administrator. Click the Add provider button and select the SAML2 SSO option to access the metadata URL.
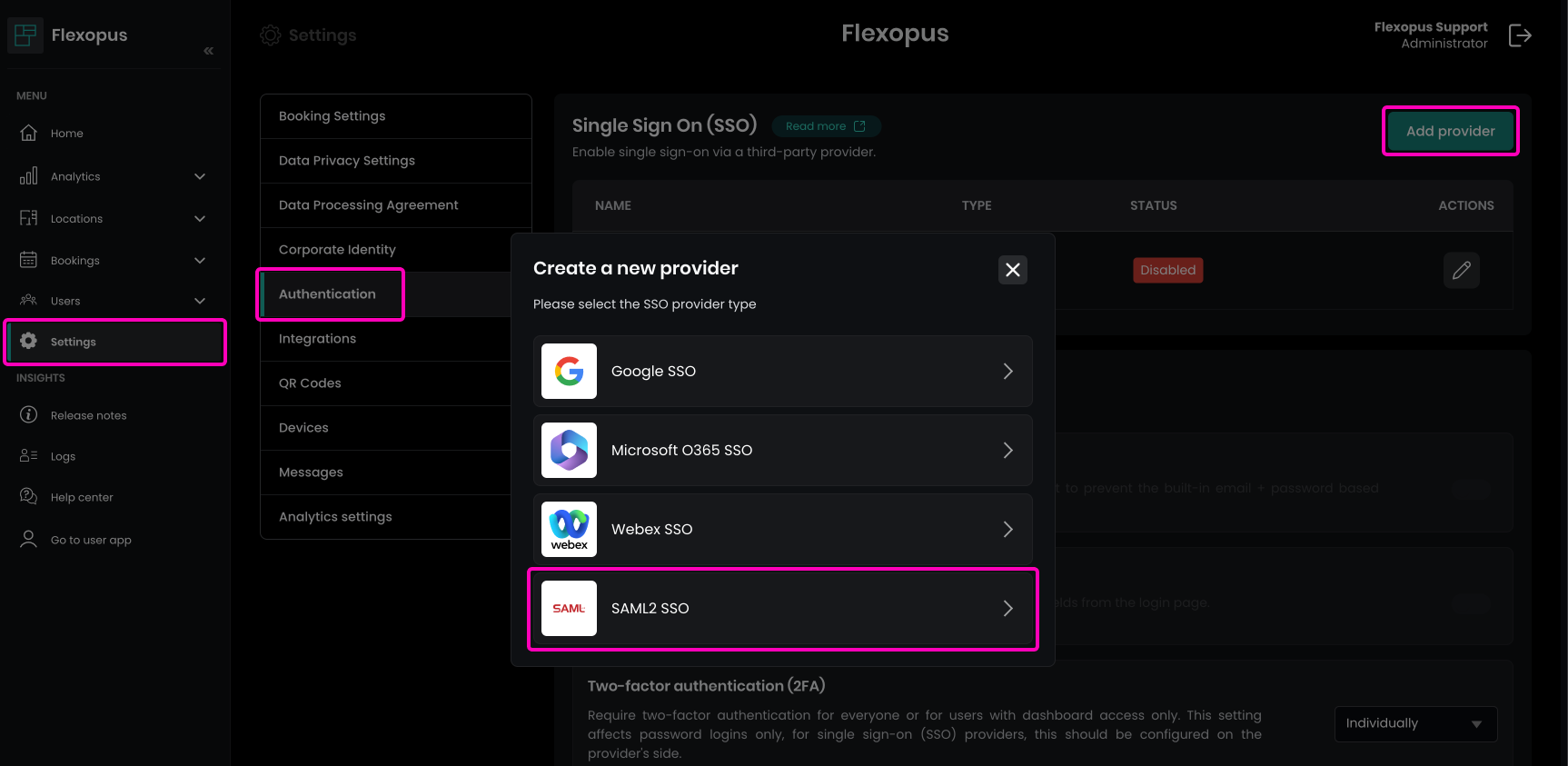
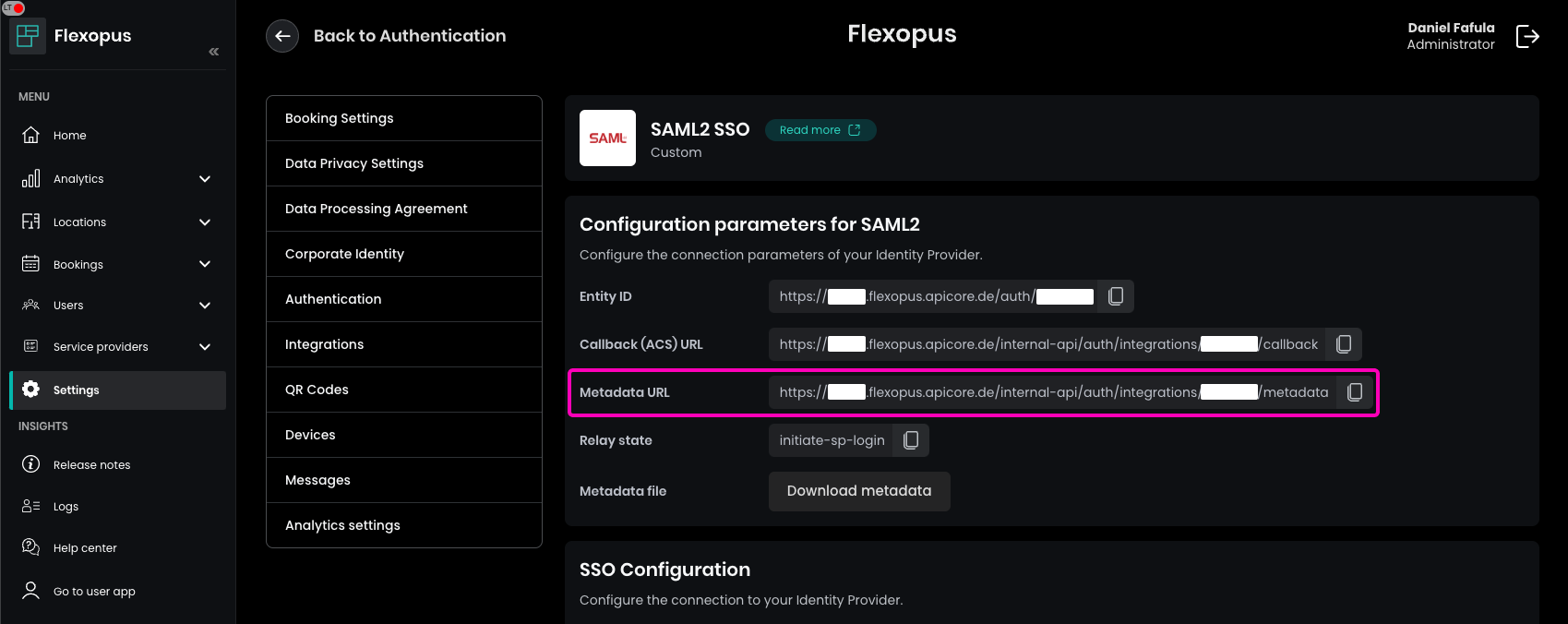
Copy the URL into Ping Identity and click on the Import button.
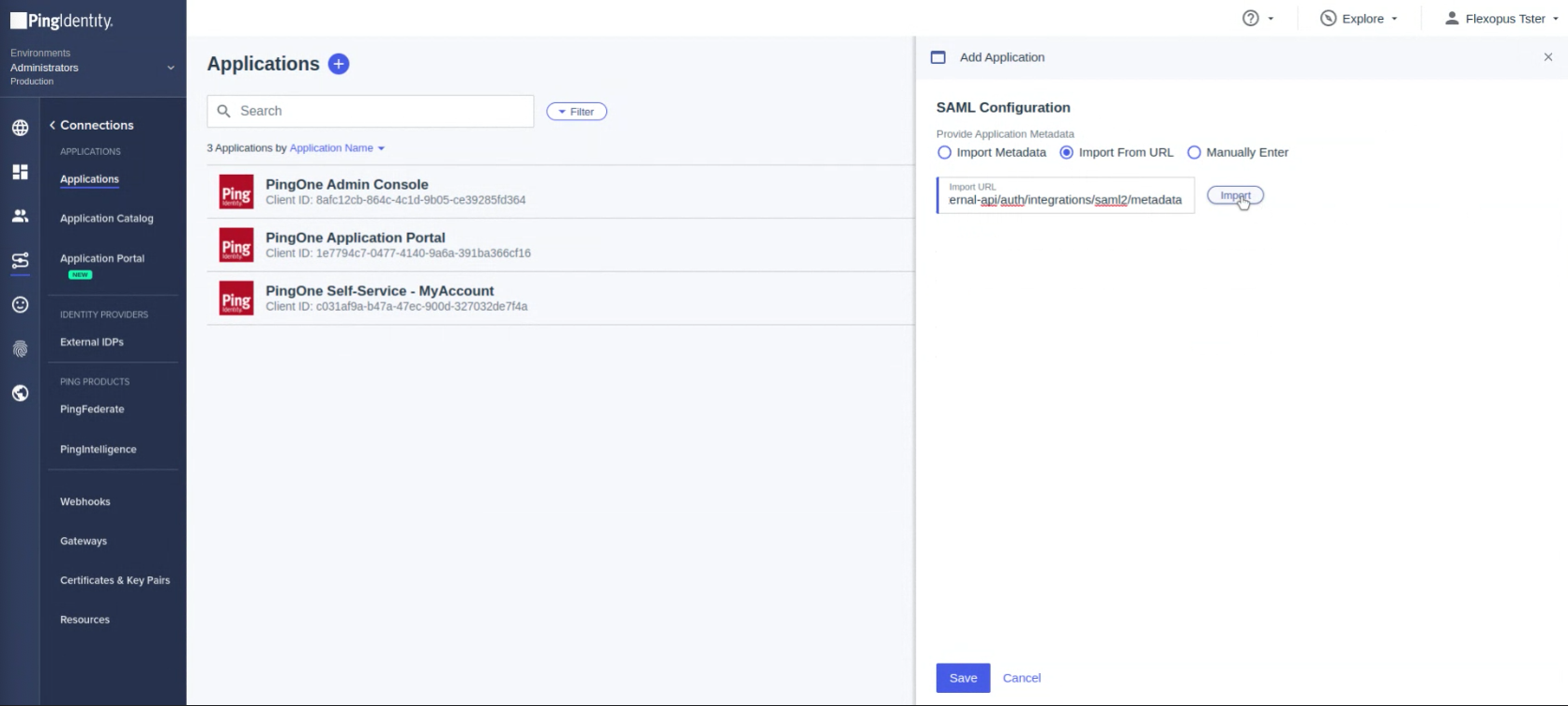
The URL will be imported automatically on the next step. Click on Save
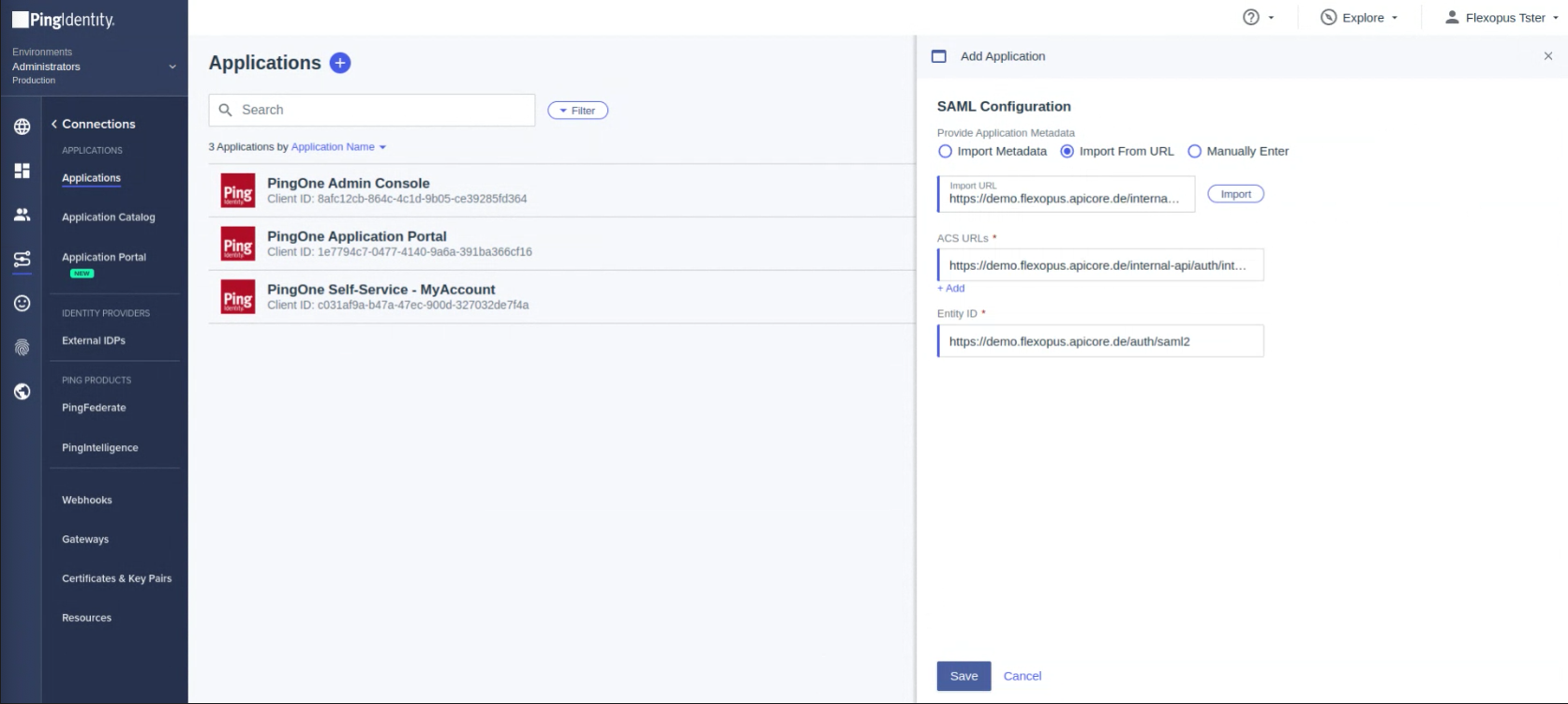
STEP 2 - Attribute mapping
As next, configure which attributes shall be exchanged between Flexopus and Ping. Set the attributes as listed below.
| Attributes | PingOne Mappings | Note |
|---|---|---|
| saml_subject | User ID | required |
| http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress | Email Address | required |
| http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn | Username | required |
| http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname | Family Name | required |
| http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname | Given Name | required |
| http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name | Formatted | required |
| department | Type | optional |
| jobtitle | Title | optional |
Once you configured the attributes, you will see the Connection Details. Copy the IDP Metadata URL.
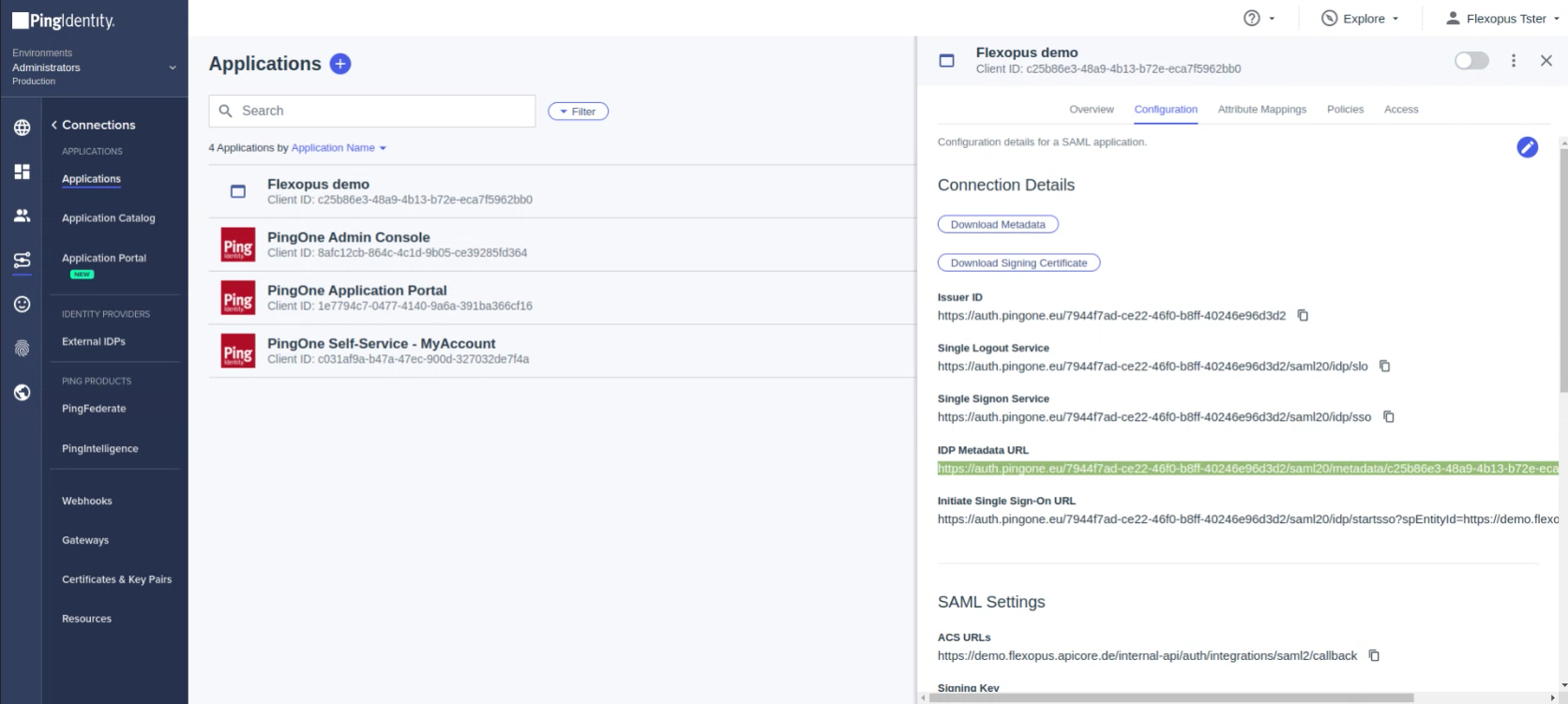
Click on the toggle button in the top to activate the connection:
STEP 3 - Configure Flexopus
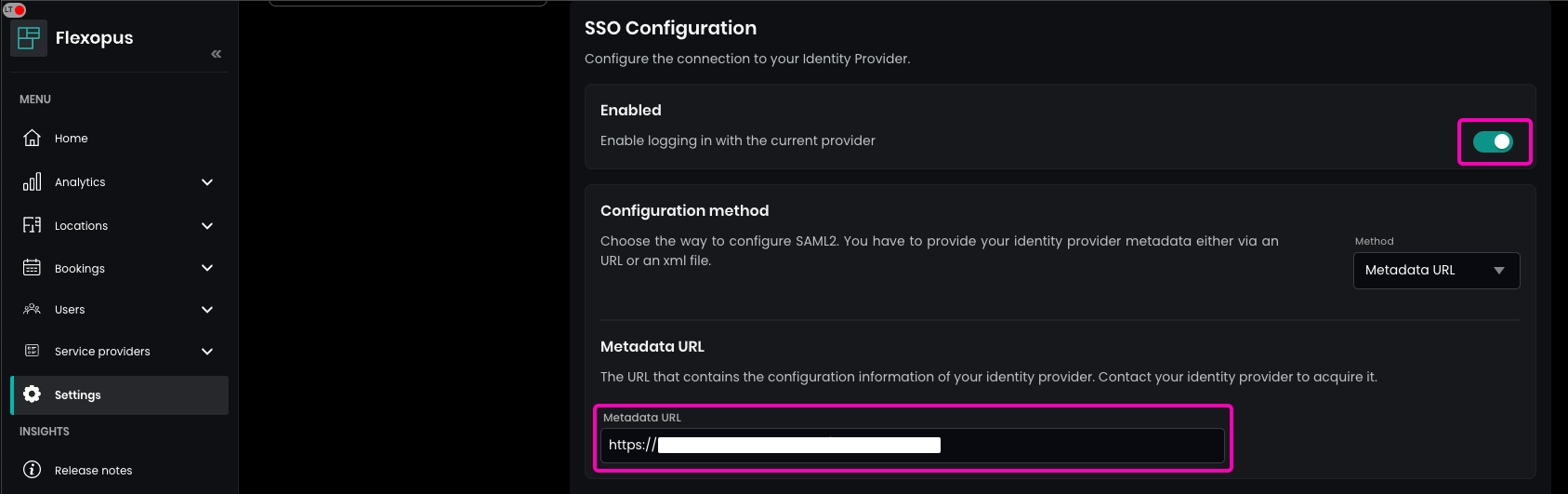
In Flexopus, navigate to Dashboard > Settings > Authentication and select the created SAML2 Provider. Enable the SAML2 SSO and paste the metadata URL in the configuration.
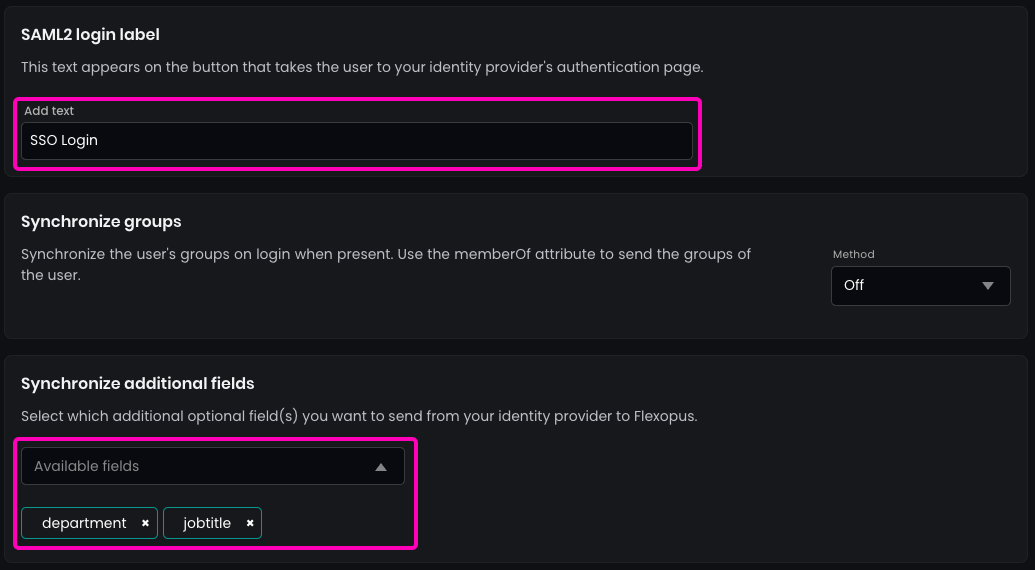
Enter the name of the SAML2 Login button, which will be displayed on the login page. Recommendation: SSO Login.
(Optional) Enable the synchronization of the fields configured in the SAML2 settings, such as jobtitle or department.
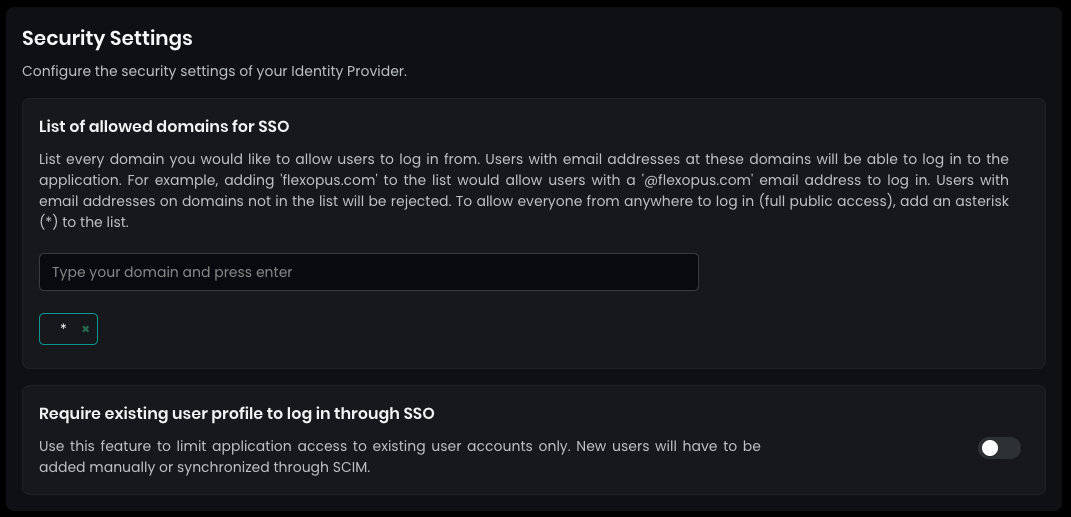
In the security settings, set the allowed domains for SSO to * (star) and press ENTER. This allows any user configured in your directory to log in.
By default, SAML2 SSO users are registered automatically after their first login. This simplifies setup, as user profiles don’t need to be created manually beforehand. However, you can disable this setting if needed (not recommended).
STEP 3 - Configure who can log in
If you try to log in now into Flexopus, you will see an error message, since you did not configure who can or cannot log in from your Ping user directory. Assign a test user to the application and test the connection to Flexopus.
Open the settings and decide which user or group can log in into the application. It's recommended enabling the login for the whole organization if you don't have any reasonable limitations in place. In this case, you don't need to maintain the user's access for the login, and you can reduce the number of possible support cases regarding the login configuration.
OPTIONAL - SCIM API
Optionally, you can also configure a user and group provisioning between Ping Identity and Flexopus via the SCIM API.
The following info and links may help you to configure SCIM:
For the SCIM connection, you need to install the SCIM Provisioner application of Ping Identity and configure the connection there.
Configuration of your on-premise SCIM Provisioner server can be found here: Connectors > PingFederate
Go to your Flexopus Dashboard as an administrator and visit the page Dashboard. Go to Settings > Integrations. Here, you can view the Tenant URL and generate the SCIM API token.
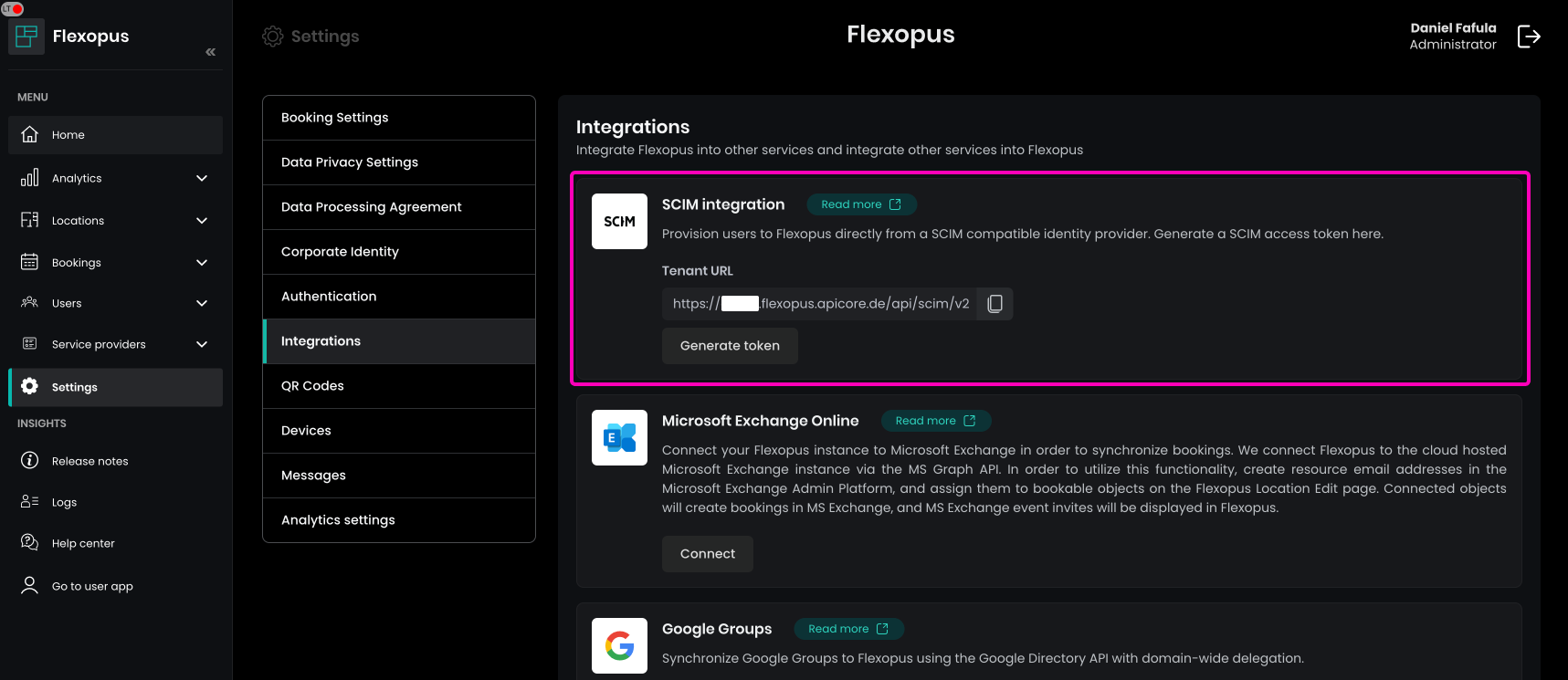
SCIM connector base URL: https://{your-flexopus-domain}/api/scim/v2
Authentication Mode: HTTPS Header
Unique Identifier for users: upn
SCIM Version: 2.0
Flexopus only supports the provisioning of flat groups.
Make sure not to sync more attributes than necessary. The required attributes are the same as the SAML2 attributes. Only one extension is needed to add them: The DisplayName should be sent as a single string (first name and last name combined).
You may also find additional information about SCIM in this article:

Trouble Shooting / FAQ
I got a 500 Error during the login.
In case you get a 500 error, you may have misconfigured the URLs or the attributes. Check the settings based on the manual once again. If you can not find the issue, contact us via support@flexopus.com. We have server logs to see where the problem lies.
Can I change the UPN of the users?
As you may know, UPN stand for UNIQUE principal names. Unique attributes shall never change, especially the UPN of the users shall remain the same. It can be a number or anything else. External application are identifying users based on their UPN, if you change you may risk creating a new user within Flexopus. Still, you may have a reason to change the UPN. In this case, contact us via support@flexopus.com. We can assist you by deleting the UPNs and the External IDs of the user to allow you the change of the UPNs in your IdP.
Can I also synchronize the user profile pictures?
Unfortunately, the SAML2 SSO protocol does not support the synchronization of profile pictures.
I saw an attribute costcenters. What is it doing?
Indeed, we have an additional attribute, which is called costcenters. The feature is currently in a BETA testing phase. More information will follow.
Does Flexopus support Identity Provider (IdP) Initiated Single Sign-On login?
Yes and No. We provide a workaround for the IdP initiated logins. You need to configure the initiate-sp-login parameter for the RelayState. This will convert the IdP initiated login request into an SP initiated login. In this way, we can ensure a secure login process.
Reason: A classical IdP initiated login would enable a man in the middle attack for hackers. Through an SP initiated login, we can avoid it. This article explains the reasons in more details: https://www.identityserver.com/articles/the-dangers-of-saml-idp-initiated-sso
.
