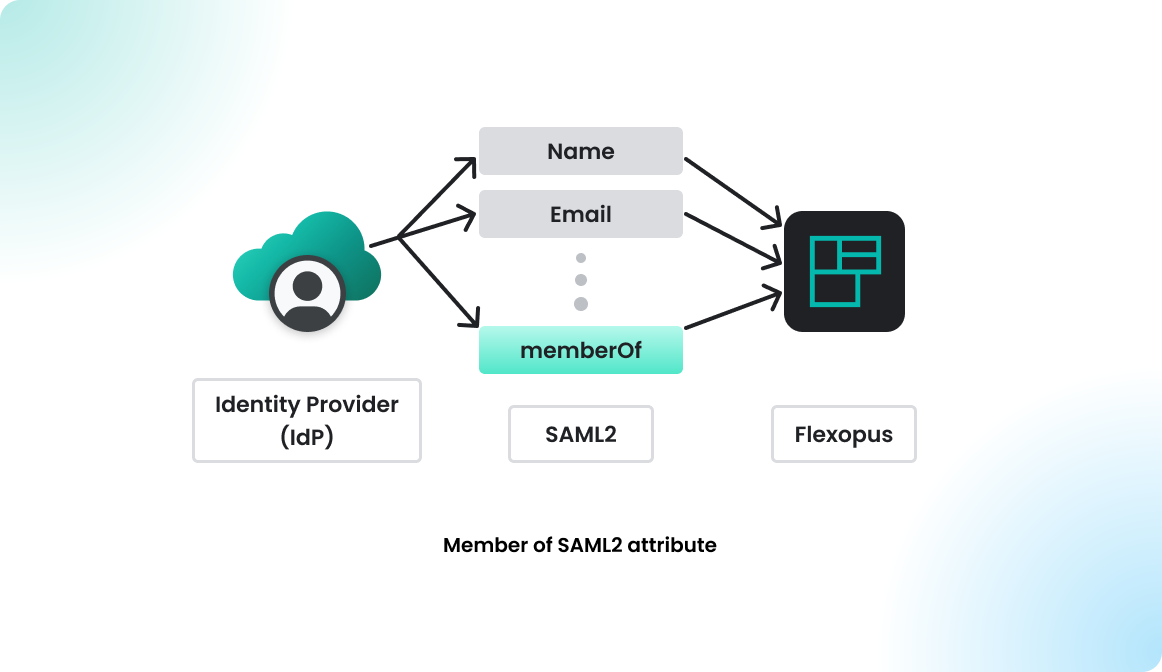
memberOf SAML2 attribute
Synchronize groups via SAML2
Flexopus implemented the standard SAML2 Single Sign-On protocol, which is supposed to work with any identity providers that follows the SAML2 standard. Often it's not only required to set up a Single Sign-On configuration for the login, but it's also necessary to exchange group memberships. This way, the user can access the right Flexopus resources after the first log in.
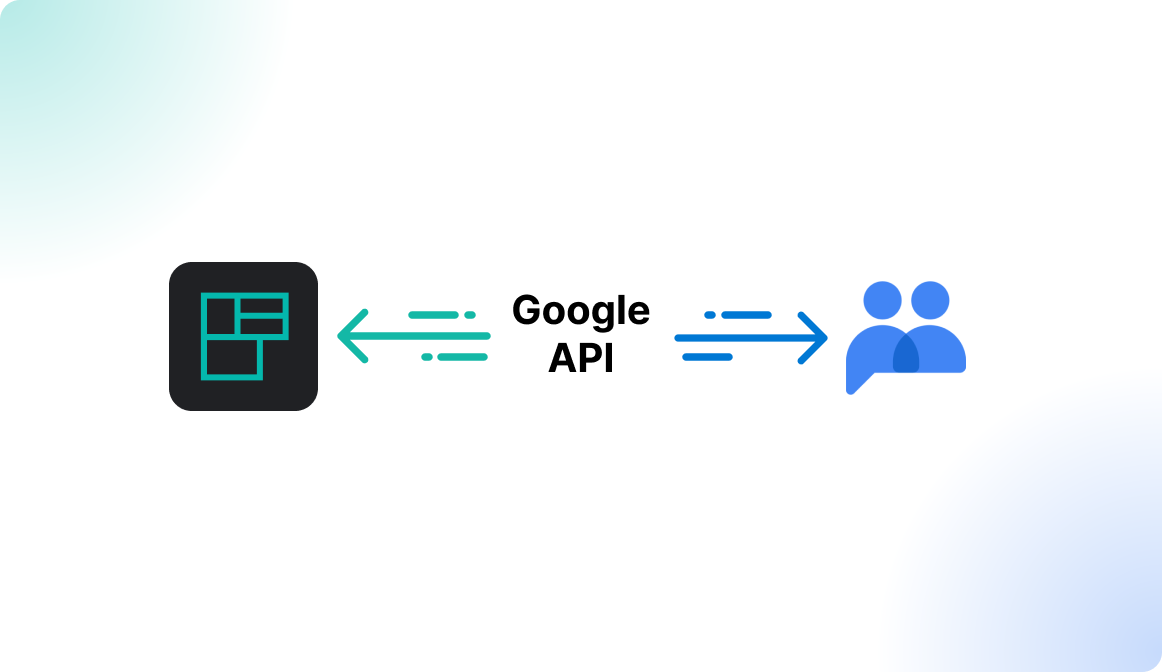
Some identity providers provide an API to synchronize groups in real time. Such integrations are in place at Google via the Google Management API and at Microsoft via the SCIM API.

Other identity providers, such as Microsoft AD FS or KeyCloak, unfortunately lack the capability to synchronize user groups via the SCIM API. As a workaround, we enable user groups to be exchanged as an additional attribute during the SAML2 authorization process, specifically through the attribute called memberOf.
memberOf attribute.Instruction Manual
We assume that you already successfully configured the SAML2 integration between your identity provider and Flexopus, if not, please visit:
STEP 1 - Configure Flexopus
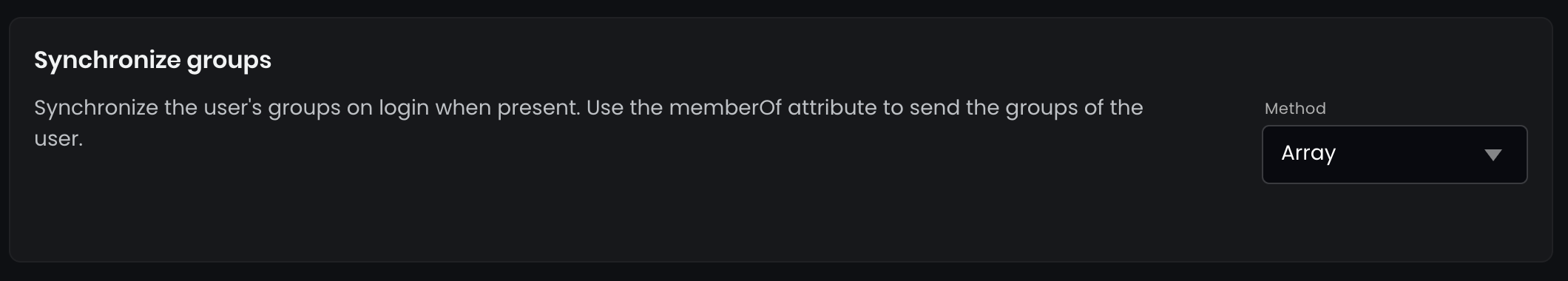
Navigate in Flexopus to Dashboard > Settings > Authentication as an administrator. Click on the preconfigured SAML2 provider and locate the synchronize groups setting, which is turned off by default. You can select from the following options:
- Off - No group synchronization.
- Array - Enables group synchronization using an array format.
- memberOf - Synchronizes groups based on the
memberOfattribute.
You can see the following options listed:
AD FS OPTION
Known IdPs require this option: Microsoft AD FS
The AD FS option will send the groups in a so called LDAP Array. The first CN will be the name of the group:
["CN=Group1,CN=...,DC=...,OU=Flexopus,OU=Org", "CN=Group2,CN=...,DC=...,OU=Flexopus,OU=Org"]
ARRAY OPTION
Known IdPs require this option: KeyCloak
The ARRAY option will send the groups in a classic array:
["Group1", "Group2"]
COMMA SEPARATE OPTION
This option will send the groups in a comma separated list:
Group1,Group2
STEP 2 - Configure your IdP
You need to configure which attributes shall be synchronized between your identity provider and Flexopus. Connect the according attribute in your identity provider with the memberOf attribute:
'memberOf' => [
'memberOf'
]
STEP 3 - Reduce session time
With SAML2, groups are sent to Flexopus only when the user initiates a login. To ensure daily group synchronization, consider setting a lower session time, such as 24 hours. This setting prompts users to log in at least once a day, enabling consistent group updates.
To configure this, navigate in Flexopus to Dashboard > Settings > Data Privacy Settings and adjust the Session lifetime. Since users typically have an active session with your identity provider, the login will usually be a simple one-click process.
Important notes
Limited request size
Note: The memberOf attribute is part of a request, for logical reasons you can not send an unlimited number of groups through this array. If the limit is reached, no groups will be sent. The limit is depending on the sending and the receiving side. For example, Microsoft limits is: Learn more here. In general, you should not send more than 100 groups via this attribute.
Identifying groups
In Flexopus, groups are identified by unique names. If Flexopus receives a group with a name that already exists as an internal group, it converts that group into an external group. When Flexopus receives a group with a new name, it automatically creates it as an external group.
Internal vs. external groups
After login, any groups received through memberOf are handled as external groups and will be attached to the user. Any other external groups not included in the received list are detached from the user, while internal groups remain unchanged.
Learn more about the groups here:
Trouble Shooting and FAQ
Can I only add one external group to the user and keep others?
External groups are managed via the memberOf attribute in this configuration. The single source of through is what we receive with this attribute. Make sure you send all external groups that suppose to be associated with the user.
Can I configure the memberOf synchronization with multiple identity providers at the same time?
No. This is not supported. We can support the groups synchronization only for one identity provider.
Can I use SCIM and the memberOf attributes parallel?
No. This is not supported. We can support the groups synchronization only for one identity provider.



