Microsoft Office 365 OAuth SSO
Introduction
You can activate an OAuth2.0-based Microsoft O365 Single Sign-On (SSO) in Flexopus. With Microsoft OAuth SSO, you essentially allow login access for all users with a Microsoft O365 account. You can then restrict access based on domain settings, determining which emails are allowed or not allowed to log in.
Read the article here.
During the setup process, we activate the interface for Microsoft Office 365 users for your cloud tenant and restrict the login option to email addresses with the domain @company.com. Afterwards, your employees can authenticate directly with their MS365 credentials.
When they log in for the first time, Flexopus automatically creates a new user with their name and email address in the backend. You can then assign special rights (e.g., Location Manager, Admin) or assign user groups to the user. An authentication check is performed for each subsequent login.
Configuration Manual
STEP 1 - Activate Microsoft SSO
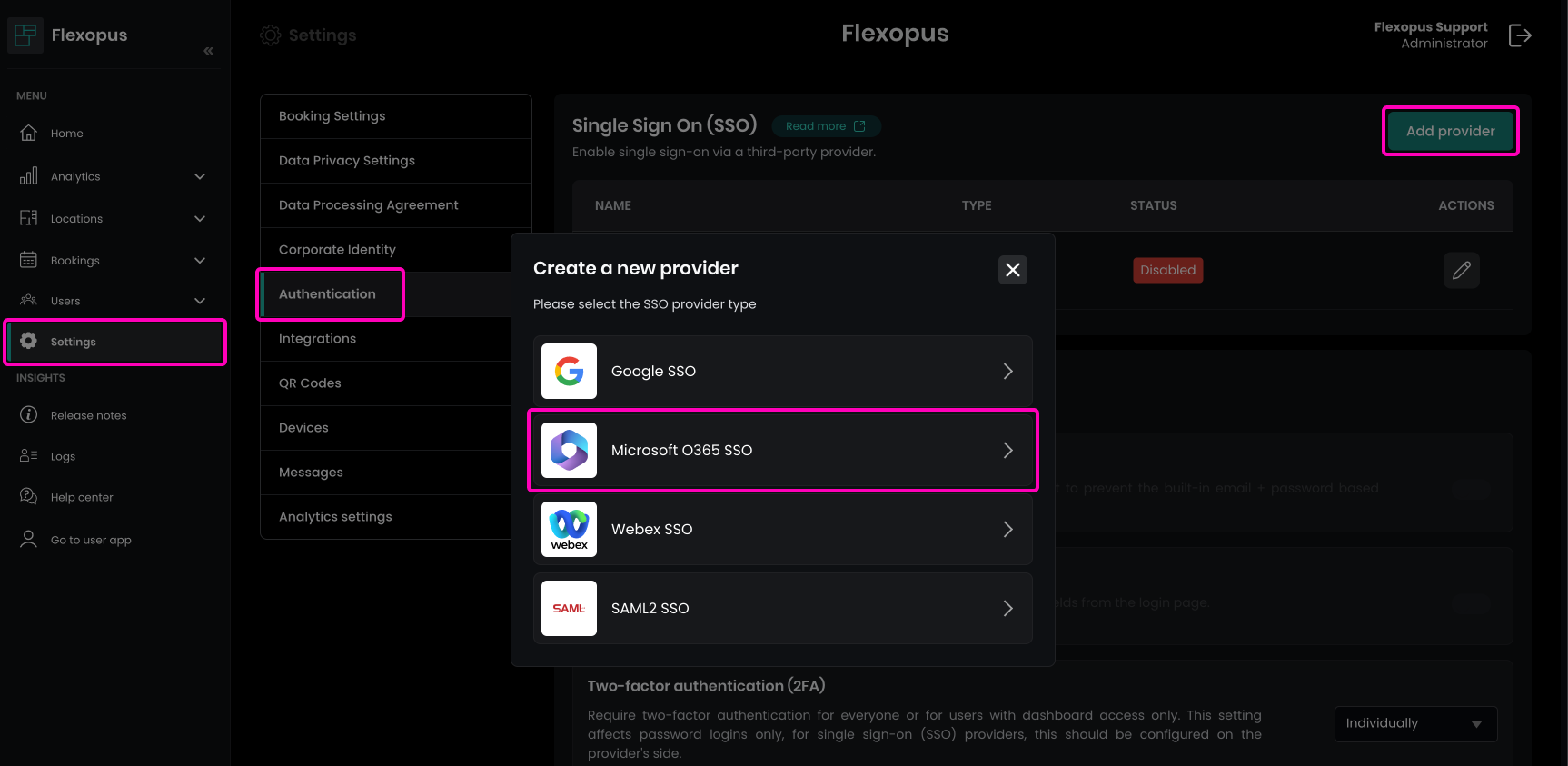
Navigate in Flexopus to Dashboard > Settings > Authentication and create a new provider. In the pop-up, select the option Microsoft O365 SSO.
Enable the integration and set the List of allowed domains for SSO setting to specify which domains are allowed to log in, such as: my-company.com, my-subcompany.de.
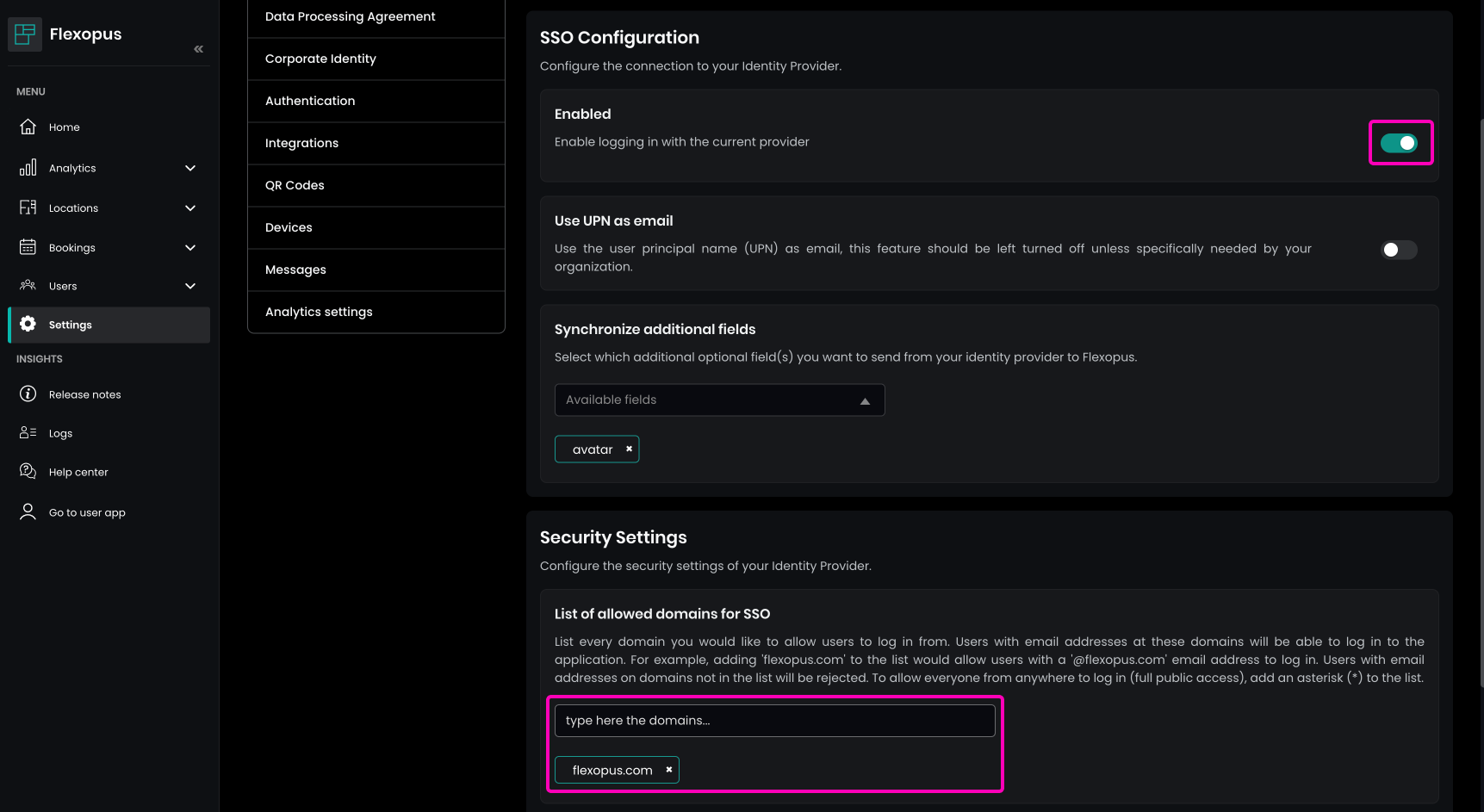
Optionally, you can enable the Require existing user profile to log in through SSO option. This ensures that only users with an existing account can log in. After activation, application access is restricted to these accounts, and new users must be added manually.
You can also configure the Use UPN as email setting to decide which Microsoft attribute to use for UPN synchronization. This is an advanced setting, and you can leave it on the default configuration.
-png.png)
Save your changes.
STEP 2 - Test the configuration
Open Flexopus in a new incognito window and test the login:
https://{your-company}.flexopus.com/ or, if you have a custom domain, go to the custom domain.
You should be able to log in with either an existing or new user, depending on how you configured the access rights in your Azure Active Directory and Flexopus.
Once Microsoft SSO is configured successfully, you can optionally disable the email and password login and enforce Single Sign-On for all users. Navigate to Dashboard > Settings > Authentication. You will find two options:
- Disable password login
You can disable all email and password login forms. - Hide login form
This option hides the login form on the main login page. However, a secondary login form (../dashboard/auth/login) remains accessible for use by a backup admin user.