Invite & Import Users
Overview
There are several ways to maintain and manage the user list in Flexopus. This article outlines the supported methods for importing users into the system, which include:
- Creating users with
SAML2 SSO - Creating users with
OAuth SSO - Provisioning users via the
SCIM API - Provisioning users with
Google Groups - Importing users via
REST API - Importing users manually
- Creating users manually
Create users with SAML2 SSO
You can connect your preferred identity provider to Flexopus via SAML2 for single sign-on (SSO). This allows users from identity providers such as Microsoft Azure, AD FS, Google, Okta, Ping, etc., to log in using their existing credentials for authentication.
Once Flexopus is connected with SAML2, you can control which users are allowed to log in through your identity provider. Upon the user's first successful login, their profiles are automatically created in Flexopus using attributes like UPN, email, and name. This eliminates the need to manually add users one by one.
Additionally, you can disable email and password-based login, forcing users to log in through SSO. Access to Flexopus can also be revoked directly in your identity provider if needed.
Learn more about SAML2 integrations:
We created a step-by-step instruction manual for the most commonly used Identity Providers as well:

Create users with OAuth SSO
You can connect Flexopus via OAuth SSO with providers like Google, Microsoft 365, and Webex. This offers a more flexible solution for single sign-on (SSO), allowing users to log in and have their profiles automatically created in Flexopus.
SAML2 instead of the OAuth options for SSO login. With a SAML2 connection, you have greater control over which users are allowed to log in. In contrast, with OAuth SSO, control is limited to the domain level.If you connect Flexopus with Google OAuth for single sign-on, this would initially allow all Google users worldwide to log in to your Flexopus instance. However, you can apply a domain-based filter to restrict access, ensuring that only users with a specific domain can log in. For example, you could enable login exclusively for Google users with a @flexopus.com email address.
Learn more about the supported OAuth connections:
Provision users via the SCIM API
Some identity providers offer the option to provision users via the SCIM API. This allows you to automatically import users and groups into Flexopus, independent of their login attempts. With this method, user profiles can be created before the first login. Flexopus has implemented SCIM API v2, which is designed to work with any identity provider that also supports this version. This makes user provisioning seamless and efficient.
Due to our current knowledge, the following identity providers are supporting SCIM: Azure Active Directory, Okta, Ping Identity. We also created a step-by-step instruction manual on how to configure them:


Provision users with Google Groups
To automatically create users, you can use the Google Groups integration in Flexopus. This integration allows you to synchronize groups and their associated users via the Google API. While Google does not offer the SCIM API, this integration serves as an equally effective alternative for provisioning users independently of their login attempts.
Learn more here:
Import users via REST API
Besides manual entry, there is a simple alternative to import users into Flexopus: the REST API. This allows you to upload a list of users via a dedicated interface. You can upload files in various formats such as CSV, TXT, ODS, XLS, or XLSX.
To use this method, you need an API token. You can find instructions on how to generate one in this article:
You can find the API documentation here::

To import users via the API, use the following endpoint:
POST /api/v1/users/import
This endpoint requires authentication using a Bearer Token and accepts multipart data as input with the following parameters:
file <file>(required):
The file containing the user list to be imported. Accepted file formats: CSV, TXT, ODS, XLS, and XLSX.update <boolean>(default: false):
Determines whether existing users should be updated.deactivate <boolean>(default: false):
Specifies whether users not present in the list should be deactivated.restore <boolean>(default: false):
Determines whether deactivated users present in the list should be reactivated.
Dashboard > Users > Import / Export.The following cURL request demonstrates how to import users. This example will.
Deactivateevery user not present in theusers.csvfile.Createevery user present in theusers.csvfile but not already in the system.Updateand (if deactivated) re-activate every user present in both theusers.csvfile and the system.
curl https://<your-domain>.flexopus.com/api/v1/users/import \
-H "Accept: application/json" \
-H "Authorization: Bearer <your-token>" \
-F "file=@./users.csv" \
-F "update=1" \
-F "deactivate=1" \
-F "restore=1" \
-F "dry_run=0"
After uploading, the API returns a JSON response detailing the performed actions:
{
"dryRun": false, // dry_run flag from the request
"created": [2, 3], // row indices for freshly created users
"updated": [4, 6], // row indices for updated users
"deleted": 0, // the number of deleted users
"skipped": [5, 8], // row indices for unchanged users
"errors": [7], // indices for rows with errors
"errorMessages": { // object with messages for every error
"7": { // row index of error
"email": [ // column with error
"The email must be a valid email address." // error message
]
}
},
"rows": 7, // total number of processed rows
"filename": "users.csv" // name of the uploaded file
}
This response helps you track the import process and quickly identify any errors.
Import users manually
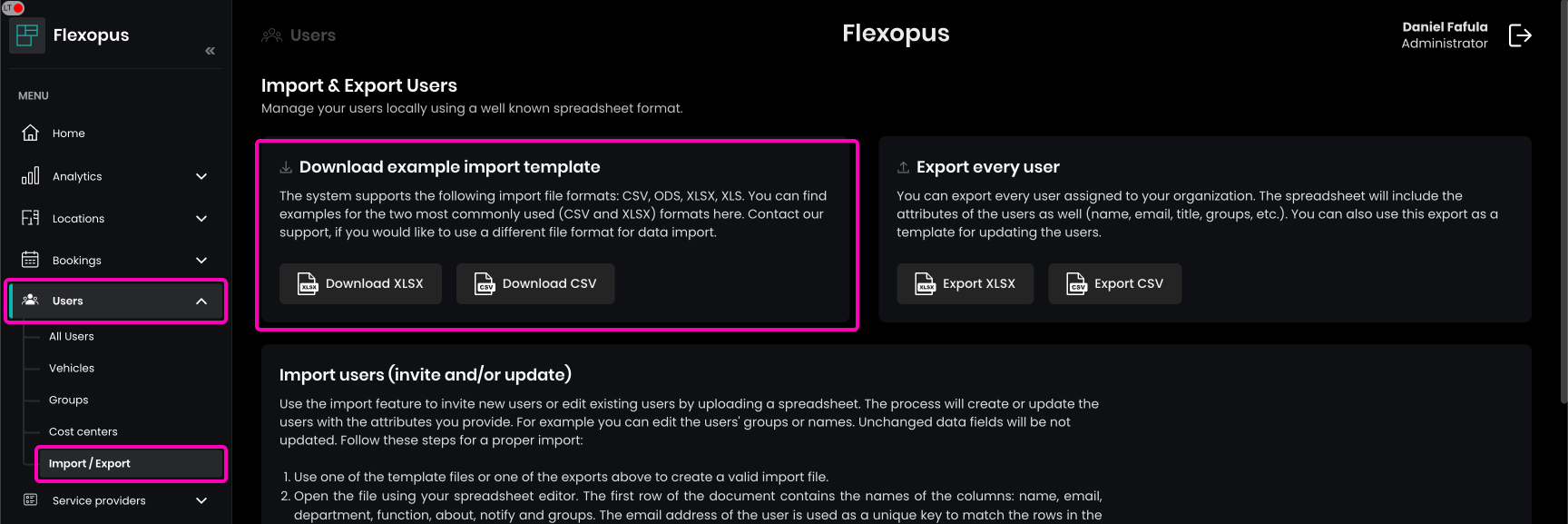
As an administrator, you can also upload users into Flexopus manually on the dashboard. Navigate to Dashboard > Users > Import / Export.
First, download one of the provided import templates as an Excel file XLSX or as a CSV file. Alternatively, you can also export all existing users and edit them by using the export function.
To import the updated file, a file upload can be found at the bottom of the page.
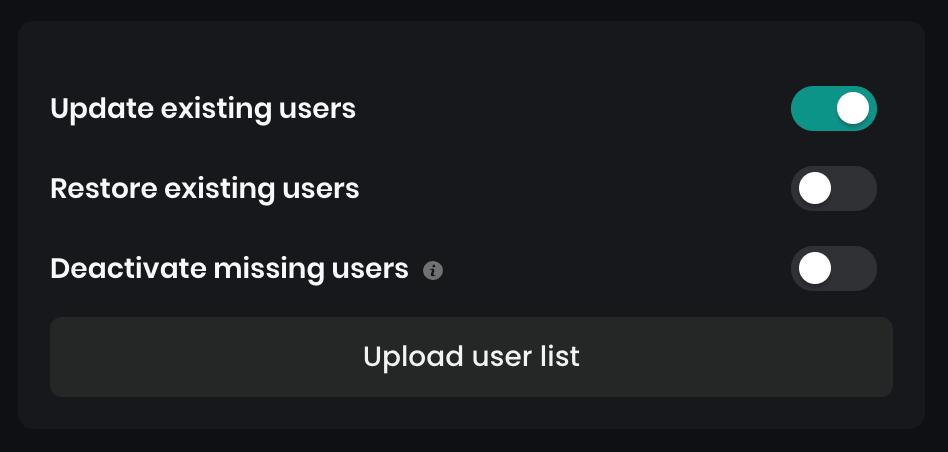
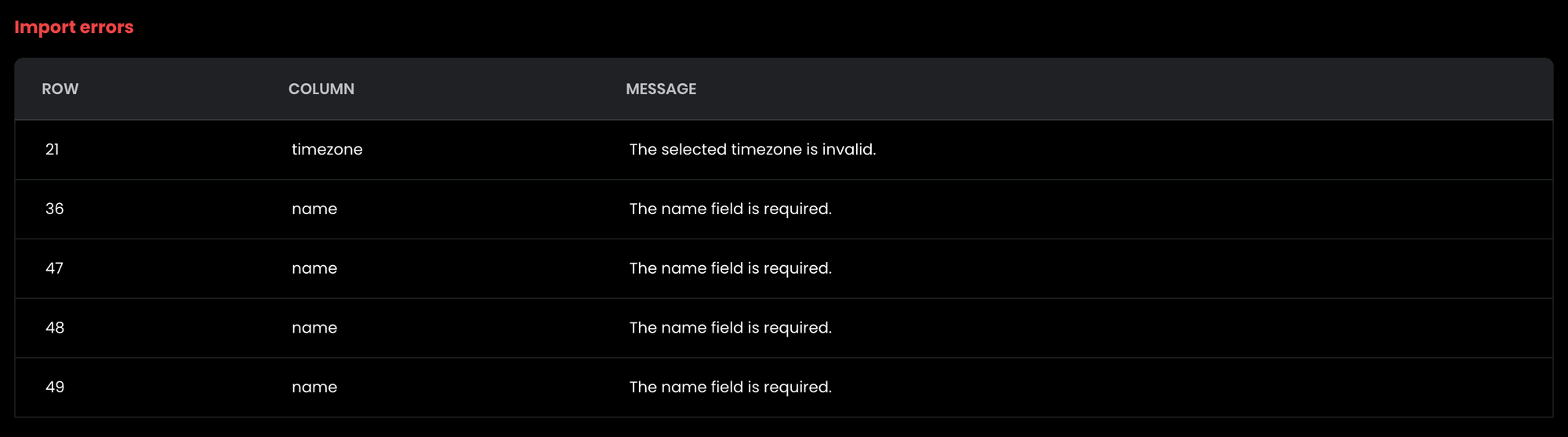
Update existing users option. This will overwrite the data of existing users and not skip them.The following file formats are accepted: CSV, ODS, XLSX, XLS. After the upload, the application will validate the file. In case the file or the file entries are invalid, you will get an error message.
Create users manually
You can also create and invite users manually in Flexopus, though this is the least recommended method as it requires the most effort and is not optimized. Before proceeding with this option, consider using one of the other methods mentioned to maintain the user base more efficiently.
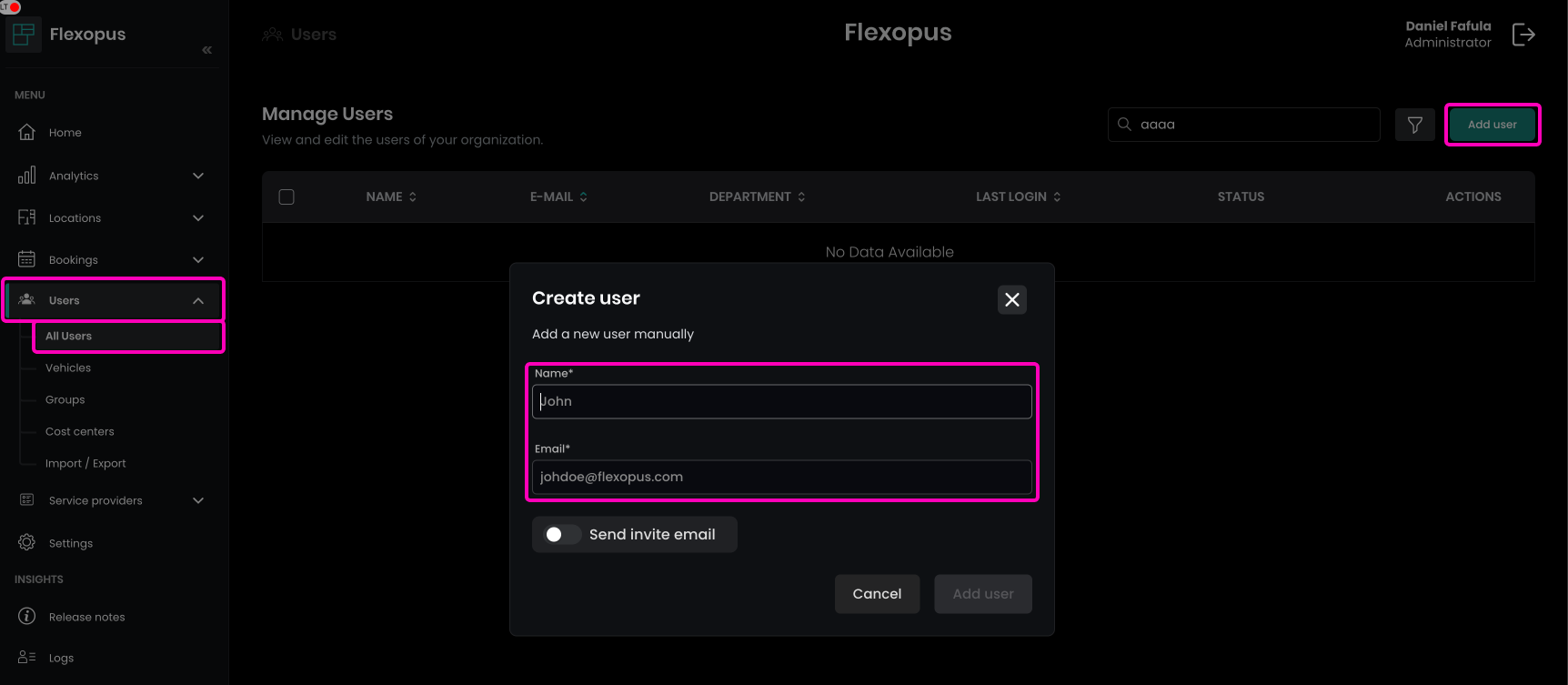
To create a user manually, follow these steps:
- As an administrator, navigate to
Dashboard > Users > All Users. - Click on the
Add Userbutton. - Enter the user's name and email address.
- Optionally, you can send an invitation message to the user.
It's advisable to explore other options before using this method to save time and resources.
Once a user is created, their email address will remain unverified. The user can set a password either through the welcome email or by visiting the login page and requesting a password reset email.
















